
A Directory Traversal vulnerability exists in Citrix Application Delivery Controller (ADC), formerly known as NetScaler ADC, and Citrix Gateway,formerly known as NetScaler Gateway (CVE-2019-19781). This vulnerability is being exploited in the wild.
A remote attacker could exploit this vulnerability to perform arbitrary code execution. Authentication is not necessary to perform exploitation and access sensitive files.
What is Directory Traversal attack?
Directory traversal or Path Traversal is an HTTP attack, which allows attackers to access restricted directories and execute commands outside of the server’s root directory. A path traversal attack aims to access files and directories that are stored outside the web root folder. By manipulating variables that reference files with “dot-dot-slash (../)” sequences and its variations or by using absolute file paths, it may be possible to access arbitrary files and directories stored on file system including application source code or configuration and critical system files.
Citrix Directory Traversal
Citrix ADC is an application delivery and load balancing solution that provides a high-quality user experience for web, traditional, and cloud-native applications – regardless of where they are hosted. and It also provides web application acceleration as well as a Gateway functionality. Citrix ADC and Gateway are accessed primarily via HTTPS on port 443/TCP.
A directory traversal vulnerability exists in Citrix ADC and Gateway. The vulnerability is because of insufficient sanitization of the request to the Citrix ADC server which allows the use of [../] due to which an attacker can access sensitive files and lead to remote code execution.
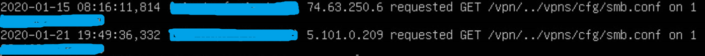
SonicWall Capture Labs observed some attack attempts trying to access sensitive file smb.conf
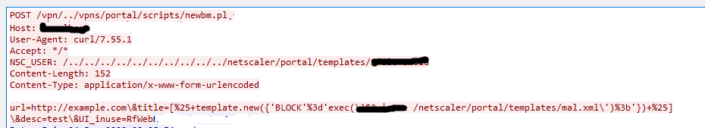
The PoC is available here. Following figure shows how an attacker can use this vulnerability to gain access to files on a victim’s machine and possibly execute arbitrary code. Citrix has listed mitigation steps and workaround here. Citrix recently released a patch for this vulnerability.

The Packet capture looks like this:
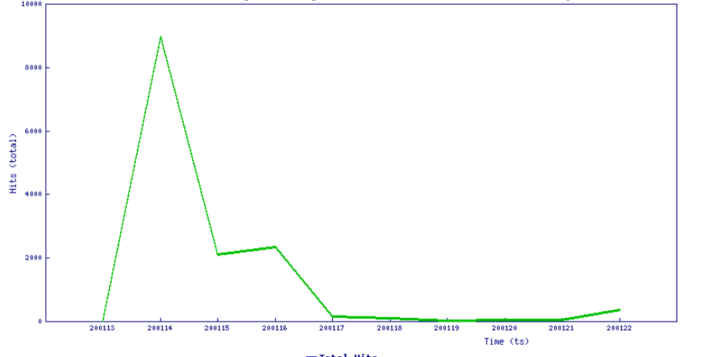
Threat Graph:
IoCs:
5.101.0.209
74.63.250.6
SonicWall Capture Labs Threat Research team provides protection against this vulnerability with the following signatures:
- IPS 14710 Citrix NetScaler ADC/Gateway Directory Traversal 1
- IPS 14725 Citrix NetScaler ADC/Gateway Directory Traversal 2
** Optrics Inc. is an Registered SonicWall partner
The original article can be found here:

