
Most of the time, threat actors in the cybersecurity landscape don’t employ advanced techniques and tools to intrude and establish a foothold within networks. Often, they disguise malicious operations by mimicking the activities of legitimate users, leaving behind little to no footprint.
Blending malicious actions with day-to-day IT activities helps attackers maintain a low profile and remain undetected for a longer period. For instance, what’s the quickest and the most common way to access a computer? By logging in. As obvious as this may sound, it’s worth noting, because stealing and using legitimate credentials to gain access is a widely used technique to compromise servers and navigate laterally under the radar.
Different ways threat actors steal credentials from servers
Apart from the typical brute-force, phishing, or shoulder surfing attacks (looking over the shoulder of a user typing a password), there are other ways to steal credentials. For instance, attackers can steal or dump credentials from the locations in which they’re stored.
Let us take a look at the various credential extraction techniques attackers use.
Dumping credentials from LSASS: This relatively old credential dumping tactic leverages a flaw within the Local Security Authority Subsystem Service (LSASS) in Windows systems. LSASS stores credentials so that users don’t have to log in repeatedly each time they want to access system resources. An attacker can dump these plaintext credentials from memory by following these three simple steps:
- Creating a memory dump from the LSASS process
- Copying and exfiltrating the memory dump via a USB drive or uploading it on a cloud drive
- Using free credential dumping tools (like Mimikatz) to dump credentials from memory
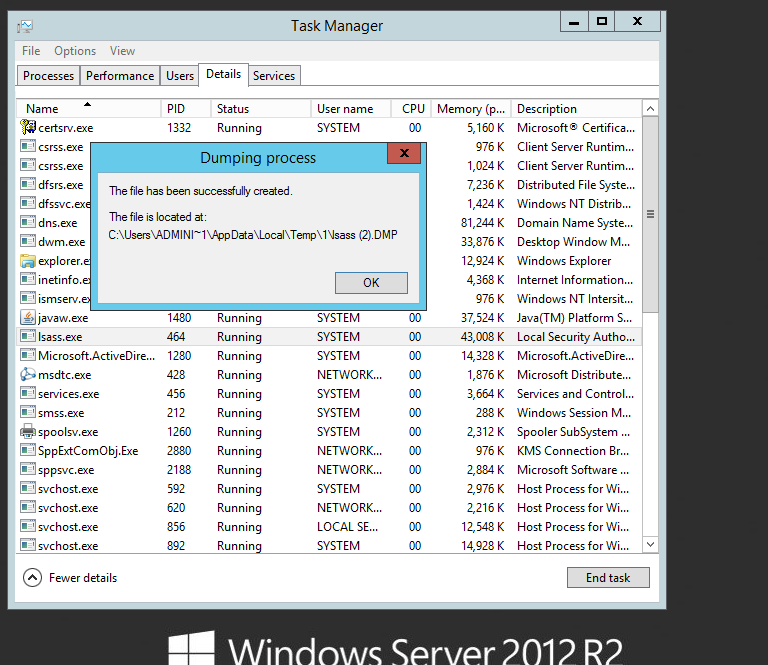
There is also a legacy protocol, WDDigest, that is used to authenticate users in Windows. But when the below registry key is enabled, LSASS keeps a plain-text copy of the logged-in user’s password in its memory.
[ HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\WDigest must be set to ‘1’ ].
Attackers often modify the above the registry key to enable the storage of ready-to-use, clear text passwords in the LSASS.
You can prevent such attacks on LSASS by running it as a protected process.
To enable LSASS in protected mode, the registry key needs to be updated to 1:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\RunAsPPL
Once you enable protected mode, all credential extraction attempts on LSASS will be unsuccessful.
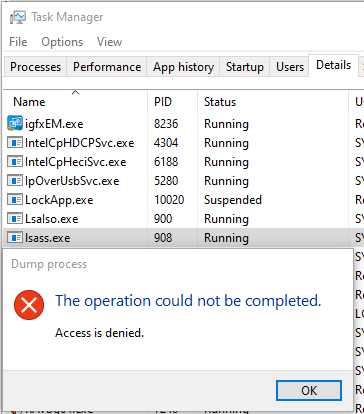
However, like we mentioned earlier, credentials are stored in different areas in a Windows system, which means more opportunities for an attacker.
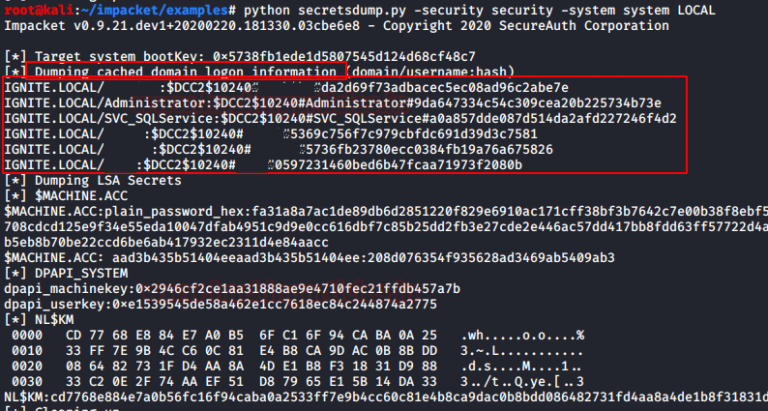
Dumping domain cache credentials
Windows also stores users’ logon information locally so that they can log on to the system even if the authentication server is unreachable. This is known as Domain Cache Credential (DCC), MSCACHE, or MSCASH hash. These hashes are stored in the Windows registry; by default, the last 10 hashes of users are stored.
This hash can be extracted from specific system and security files stored in the registry. Attackers can steal these files and later extract them to get plaintext passwords.
Active Directory Domain Database
By stealing the NTDS.dit file, Active Directory’s database, an attacker can extract a copy of every user’s password hash and can act as any user in the domain. But since the NTDS.dit file is always in use, it cannot be copied or moved. Therefore, attackers resort to the shadow copy (Volume Shadow Copy VSS) method to steal the contents of the file.
Extracting passwords from the clipboard
In the ideal scenario where you’ve secured every server from credential dumping attempts, threat-actors leverage the clipboard to extract passwords, because there’s a good chance that your users have copied usernames and passwords from a secure location (like a password vault) to enter them in a login screen.
Recording key presses to extract credentials
Attackers often strategically position keyloggers in the logon scripts of group policies or the registry. They may even create a scheduled task to record key presses to extract information entered by your users. Apart from credentials, this keylogger can also capture personally identifiable information (PII) like credit card information, passwords, Social Security numbers, and more.
Credential dumping attacks are quicker and more devastating compared to other attacks, because once threat-actors can dump the credentials of users in your domain, they can effectively impersonate any user, even your privileged users.
There are several locations that must be monitored across all your endpoints to detect credential dumping attempts. For instance, Windows systems also store encrypted credentials for popular browsers like Google Chrome in the path – AppData\Local\Google\Chrome\User Data\Default\Login Data. Free open-source tools on the internet can be used to extract sensitive credentials from this location.
Looking for a comprehensive solution that can detect and mitigate credential dump attempts in your network? Check out ManageEngine Log360!
** Optrics Inc. is an Authorized ManageEngine partner
The original article can be found here:

