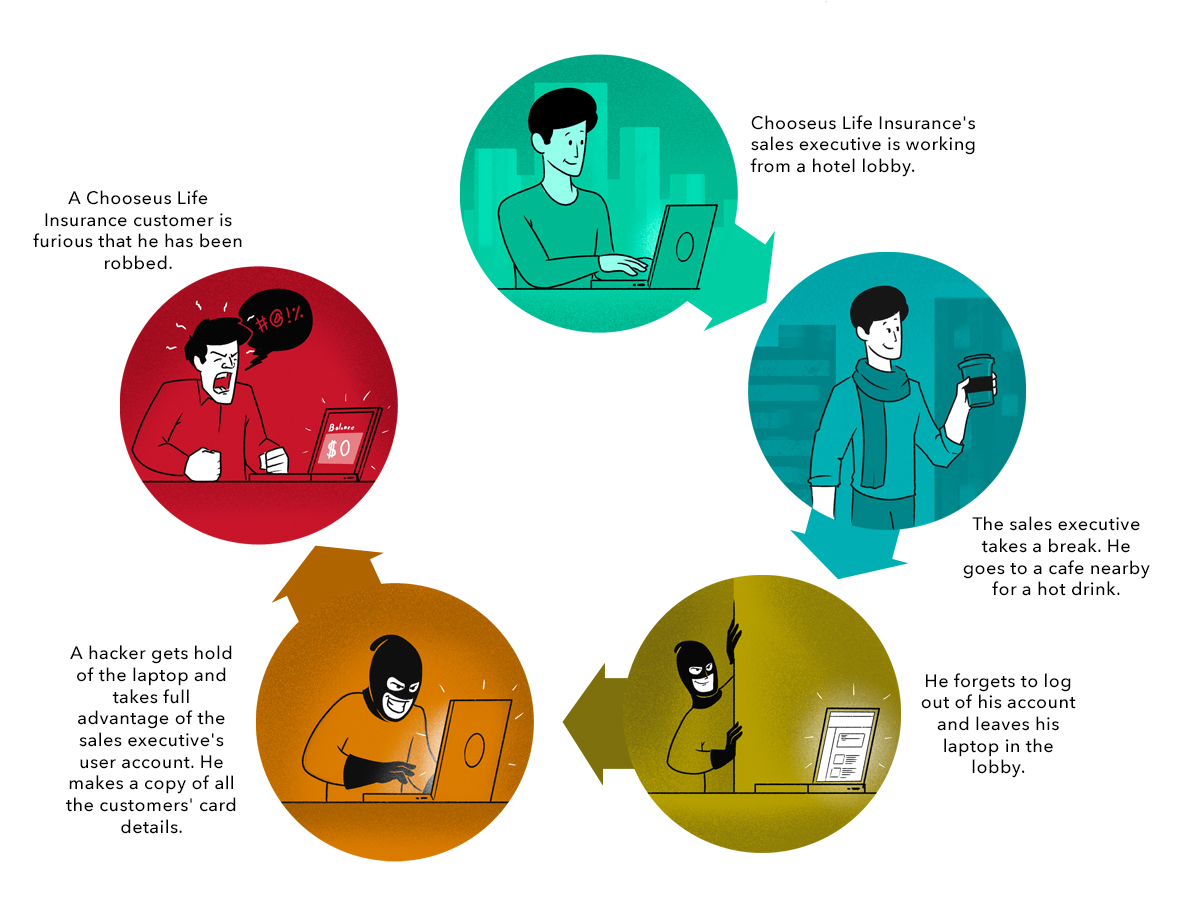
How Chooseus Life Insurance lost its customers’ cardholder details and their trustIn August 2019, reporters began flocking to Chooseus Life Insurance’s head office in Detroit after news leaked that thousands of the company’s customers had lost money due to a security breach. The CEO of this life insurance company released the following statement: “We have […]
Aruba Commercial My personal data is none of your business
Click here to learn more about Aruba’s wireless networking solutions
How is BYOD Affecting Your Business? Industry Leaders Discuss
Listen as experts from Barcoding, Inc., Motorola Solutions, and Verizon discuss the challenges and opportunities with BYOD (Bring Your Own Device). Filmed by SupplyChainBrain at the 2012 Barcoding, Inc. Executive Forum in Baltimore, MDClick here to learn more about Aruba’s wireless networking solutions
TIG – iPad in Business event, Rick Hartley, Xirrus, 31 JAN 2012
Click here to learn more about Xirrus’ wireless networking solutions
Get Network and Business Intelligence
The CTO of a large retailer describes Cisco Meraki’s cloud-managed IT solution, deployed throughout several stores, provides network and business intelligence on one simple dashboard.Visit the Cisco Meraki website to learn more: http://meraki.cisco.com.Subscribe to Cisco’s YouTube channel: http://cs.co/Subscribe.Click here to learn more about Aruba’s wireless networking solutions
LiNC 2013 Aruba Networks: Infuse Social Across the Business
LiNC 2013 with Ben Gibson CMO of Aruba NetworksLithium helps companies unlock customer passion to grow brand advocacy, drive sales, reduce costs and accelerate innovation. Lithium social software helps more than 350 of the world’s most iconic brands such as AT&T, Sephora, Univision, and PayPal build brand nations—vibrant online communities of passionate social customers. For […]
Simon Tompson – Cisco Meraki – A Network as Agile as Your Business – 10th Annual Convergence Summit
Simon Tompson of Cisco Meraki presentation at the 10th Annual Convergence Summit from Britannic Technologies.About Simon:Simon Tompson is Cisco Meraki’s Solutions Architect in EMEAR, covering technical, presentations, demos, training, blogging and social media.Simon has a long history with global leaders in data networking stretching back to the 1990s, having previously worked as an Enterprise Network […]
Simple Denial of Service DOS attack mitigation using HAProxy
Denial of Service (DOS) attacks can be especially effective against certain types of web application. If the application is highly dynamic or database intensive it can be remarkably simple to degrade or cripple the functionality of a site. This blog article describes some simple methods to mitigate single source IP DOS attacks using HAProxy. I’ve described how you would implement the techniques using the Loadbalancer.org appliance but they are easily transferable to any HAProxy based cluster
TurboTax’s Anti-Fraud Efforts Under Scrutiny
Two former security employees at Intuit — the makers of the popular tax preparation software and service TurboTax – allege that the company has made millions of dollars knowingly processing state and federal tax refunds filed by cybercriminals. Intuit says it leads the industry in voluntarily reporting suspicious returns, and that ultimately it is up to the Internal Revenue Service to develop industry-wide requirements for tax preparation firms to follow in their fight against the multi-billion dollar problem of tax refund fraud
5 Best Practices to Be a Successful Project Manager
As a project manager who’s been around a while you would have experienced a visit to the project guillotine. Perhaps, it was due to a massive schedule slip, budget overrun, or scope creep (or sometimes all three – now that’s total chaos). And, as a project manager, you were the first in line at the guillotine! In retrospect, you (always) get a feeling, “ If only I handled the project differently, it could have been a success