 The bad guys can’t do anything on your network without access. That’s why they focus their efforts on gathering as many sets of credentials as possible. You should focus there too.
The bad guys can’t do anything on your network without access. That’s why they focus their efforts on gathering as many sets of credentials as possible. You should focus there too.
The cybercriminals don’t just want to get onto a user’s endpoint and simply stop there; their goal is most commonly to monetize the attack through ransomware, cryptomining, or data theft. But, each of these attack types have one thing in common: they require access. It may be admin access to the endpoint, to a server, or to all of Active Directory; it really depends on what the attack purpose is.
According to Verizon’s latest Data Breach Investigations Report, the #1 threat tactic used in successful data breaches is compromised credentials. So, let’s stop and think about that for a moment.
There are lots of layers in your security stance, but shouldn’t your primary focus be preventing credential compromise? If it’s the one thing that most data breaches have in common, it makes sense to put a material focus on stopping that threat action. In many ways, it’s great news that you can focus on just one thing – attackers are constantly changing tactics, methods, scams, angles, etc., making it difficult for IT organizations to do little more than simply react when attacks occur.
There are lots of ways cybercriminals gather credentials:
- Phishing and social engineering
- Malware and key logging
- Leaked databases
In many cases, cybercriminals only need to acquire a single set of credentials to gain access to multiple systems and applications, as three-quarters of users reuse passwords across different accounts, and nearly half of them use the same passwords across work and personal accounts.
Stopping Credential Compromise
You can’t keep up with the changing face of attacks – there are too many and are changing too rapidly. What you can do is to focus on the one common element among attacks – the user. In every case where credentials are compromised, a user needs to be involved. So, it stands to reason that if you can train the user to be security-minded, to spot scams and social engineering tactics, and to avoid becoming a victim, you can reduce the attack surface for your organization.
You can only accomplish this with Security Awareness Training. Designed to elevate the user’s mindset to include keeping the organization secure at all times, users are continually taught about scams, tactics, social engineering, and the need for them to play a role in your organization’s security.
Stopping credential compromise is possible, but it’s going to take more than just security solutions in place; it’s going to take your users taking part in your security efforts.
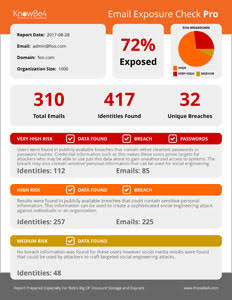
What is your actual social engineering attack surface?
We have something super cool for everyone, customers and non-customers both, and there is no cost.
Many of the emails addresses and identities of your organization are exposed on the Internet and easy to find for cybercriminals. With that email attack surface, they can launch social engineering, spear phishing and ransomware attacks on your organization.
** Optrics Inc. is an Authorized KnowBe4 partner
Find out how affordable new-school security awareness training is for your organization. Get a quote now.
The original article can be found here:
https://blog.knowbe4.com/reduce-the-risk-of-data-breach-by-focusing-on-compromised-credentials


